As we rapidly adopt digital technologies with smartphone penetration slated to reach 4 billion by 2022 and new technologies like IOT, blockchain, AR/VR and digital currencies getting ready for mainstream adoption, the need for cybersecurity has never been greater.
Market Issues
- Owning Identity is hard
- Verifying identity requires mass consensus
- Centralized systems are unreliable in long term
- Identities need to constantly remain validated and updated
- Limitations of mass adoption
- Cyber-security can no longer be a walled garden
What is Diro
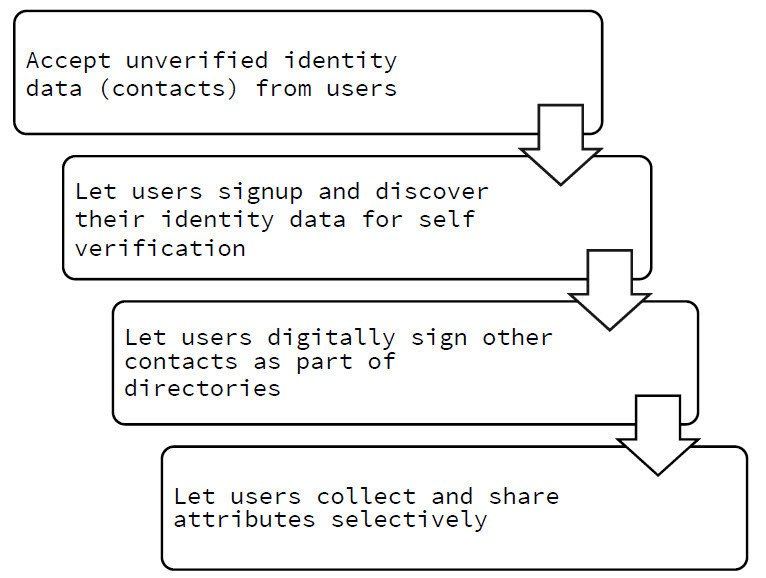
- A decentralized identity & access platform powered by crowdsourcing of contact directories.
- 100% accurate & instant KYC of 5+ billion people using cryptographically provable original documents.
- Hardened & secure social identities using crowdsourcing of contact directories.
Why Diro
- Instant Verified Legal Identities
- Hardened Social Identities
- Password-less Access
Diro Features
1- Tamper-proof Remote KYC by instantly verifying online documents:
- Document is stored along with verified SSL, timestamp and hash.
- Users can tag these documents to mobile number and multiple wallets.
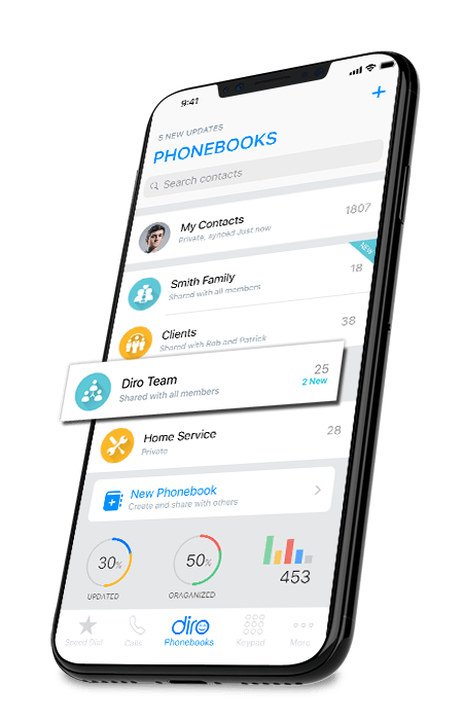
2- Crowd-sourcing to power contact directories:
- Diro uses power of crowd intelligence to automatically tag people to shared phonebooks to create the world’s defacto contacts app.
- Contacts get organized, updated & discovered automatically with complete privacy controls.
- Creating a social fingerprint for recoverable & loss-proof Identities with decentralised PKI.
3- Diro Identity Score for hardened identities:
- Score based on no. of validated connections & live interaction in Family, Friends, School, College & Co-worker phonebooks .
4- Contacts App to drive global access:
- Make your contacts go alive - be it IVR options, wait times, appointment booking or simply your miles or preferences with universal frictionless access from inside your contacts.
5- Connect silos & Eliminate password with complete privacy & PKI (Blockchain):
- Prevent external correlation with DIDs.
- Seamless Decentralized public key infrastructure.
- User profile cards to manage privacy.
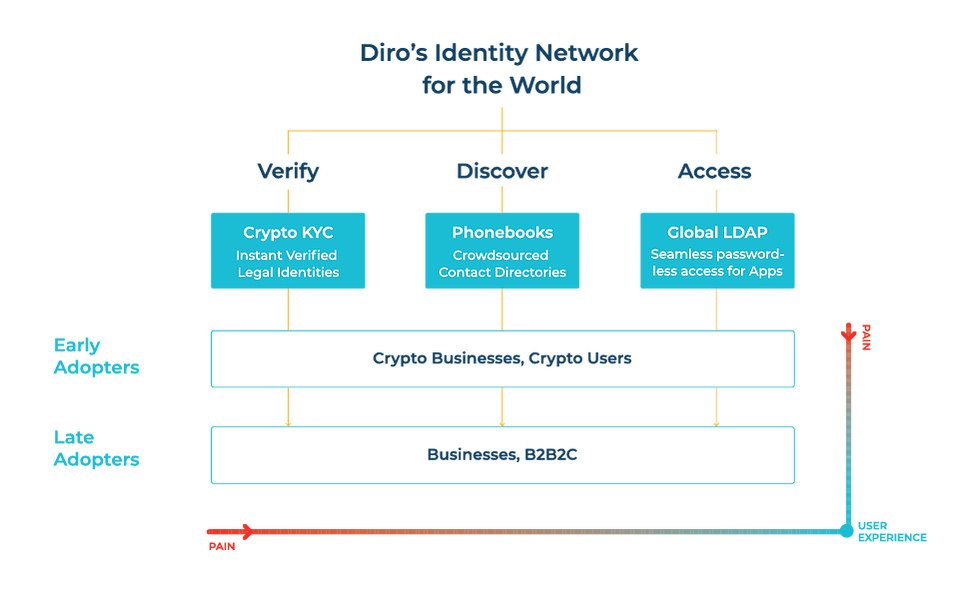
The Decentralization IAM infrastructure
The complexity of network admission control and authorization information needs to be simplified mobilefirst employee directories that match the working styles of today.
A very useful and broad architectural layering requirements were recently proposed as Semantic Identification Layers:-
A very useful and broad architectural layering requirements were recently proposed as Semantic Identification Layers:-
- Global Contact Directories
- Decentralised Identities
- Identity & Access Management (dLDAP)
The simplest way to build global identity verification is to issue certificates to identities associated with MSISDNs present in contact directories.
Finally
Identity and security for establishing trust are critical building blocks on blockchain. Contact directories or social graphs are a central component in decentralizing the identity and access management. Without using social confirmation building a reliable decentralized identity and security architecture is not possible.
✅Website: http://www.diro.io/
✅Whitepaper: https://docs.wixstatic.com/ugd/fae167_26798553a540495d9c8189932e9c088f.pdf
✅Twitter: https://twitter.com/DiroLabs
✅Facebook: https://www.facebook.com/DiroBlockchain
✅Reddit: http://www.reddit.com/r/dirolabs
✅Telegram Group: https://t.me/DiroToken
✅Bitcointalk ANN: https://bitcointalk.org/index.php?topic=3266144.msg34032664#msg34032664
✅Whitepaper: https://docs.wixstatic.com/ugd/fae167_26798553a540495d9c8189932e9c088f.pdf
✅Twitter: https://twitter.com/DiroLabs
✅Facebook: https://www.facebook.com/DiroBlockchain
✅Reddit: http://www.reddit.com/r/dirolabs
✅Telegram Group: https://t.me/DiroToken
✅Bitcointalk ANN: https://bitcointalk.org/index.php?topic=3266144.msg34032664#msg34032664
Author of article:
✅Bitcointalk username: Erik_Smuel
✅Bitcointalk profile link: https://bitcointalk.org/index.php?action=profile;u=2020517
✅Bitcointalk username: Erik_Smuel
✅Bitcointalk profile link: https://bitcointalk.org/index.php?action=profile;u=2020517
1 comment:
Thanks for this informative article, I hope you will get most positive response specially for this post. . . .
Visit Free Robux Today
Post a Comment